Introduction to DDoS Attacks and Their Impact
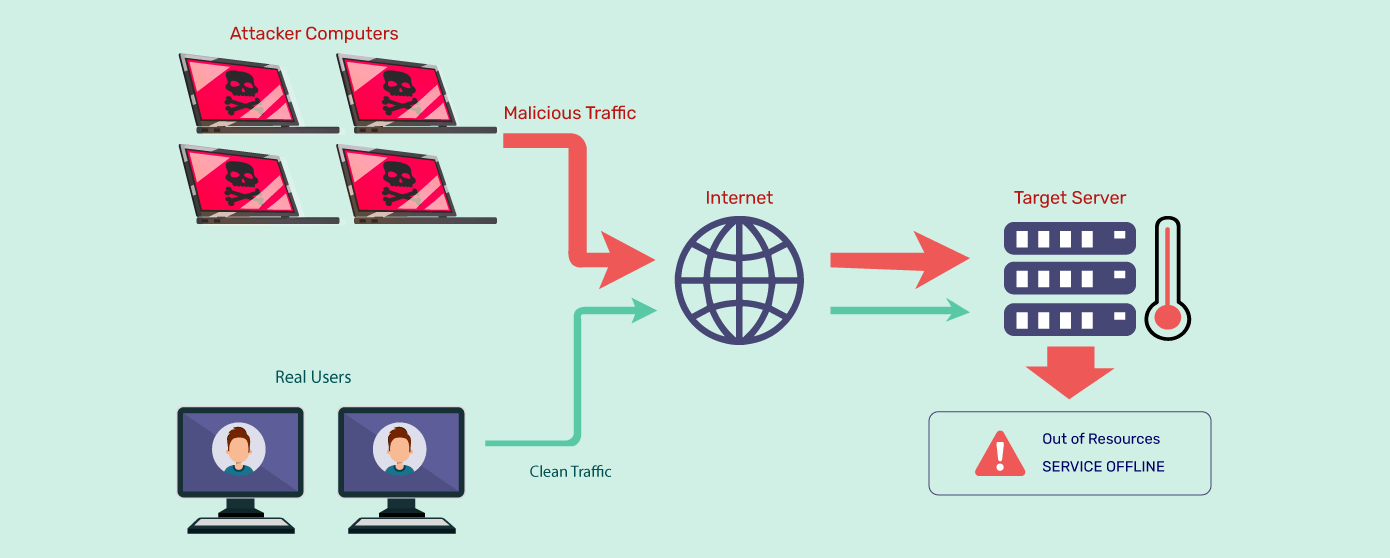
Distributed Denial of Service (DDoS) attacks significantly threaten businesses and organizations worldwide. A Denial of Service (DoS) attack is a harmful effort to impact the accessibility of a specific system, like a website or application, to genuine users. Usually, cyber attackers flood the target system with a high volume of packets or requests to cause it to be overwhelmed. If a DDoS attack occurs, the attacker will employ numerous compromised or controlled sources to carry out the attack. These attacks function by inundating a network with traffic, interrupting vital services, and stopping operations. Understanding the core aspects of DDoS attacks is crucial for devising effective mitigation strategies. For businesses seeking advanced solutions, a DDoS mitigation service can be an invaluable resource for ensuring network security and continuity.
Because of these attacks’ increasing frequency and complexity, organizations must implement proactive tactics to safeguard their infrastructure. Not addressing this threat can lead to significant financial losses, harm to reputation, and disruptions in operations. Comprehending the effects of DDoS attacks is the initial stage in developing a solid defense plan.
Recognizing the Signs of a DDoS Attack
Identifying the early signs of a DDoS attack can help prompt swift action. Common indicators include unusual spikes in traffic, network slowness, and frequent service disruptions. These symptoms often manifest suddenly and can escalate quickly, so IT departments must be vigilant and ready to act at the first signs of trouble.Spotting these signs early can significantly mitigate the impact of the attack. For instance, a sudden and unexplained surge in incoming traffic that exceeds the norm could signal a potential DDoS threat. Similarly, it’s time to investigate further if users complain about slow network performance or the inability to access websites and applications.
Effective Strategies for DDoS Mitigation
Various strategies can be employed to mitigate DDoS attacks. Implementing rate limiting is critical, as it controls the amount of incoming traffic that can reach a network. Organizations can avoid getting overwhelmed by harmful traffic by restricting the number of requests a server can handle during a certain period.
Additionally, having a well-defined DDoS response plan is essential for minimizing risks. This plan should outline the steps during an attack, including communication protocols, roles and responsibilities, and escalation procedures. Regularly updating security protocols to address new vulnerabilities and threat vectors is also critical. Combining these efforts with other security measures creates a multi-layered defense that is more effective in neutralizing threats.
The Role of Continuous Network Monitoring
Constant network monitoring is imperative for the early detection of DDoS attacks. Advanced monitoring tools can help track traffic patterns, detect anomalies, and alert administrators in real time. By maintaining vigilance through continuous monitoring, organizations can respond promptly to threats, minimizing downtime and damage. For instance, TechRepublic’s guide on network monitoring provides in-depth insights on establishing an effective monitoring system. Using such tools allows for collecting and analyzing traffic data, making identifying abnormal behavior indicative of a DDoS attack easier. Continuous monitoring not only aids in immediate detection but also helps understand long-term traffic patterns and potential vulnerabilities.
Rapid Response Tactics
A rapid response plan is critical for mitigating the impact of DDoS attacks. Training your team to understand and recognize the signs of a DDoS attack is fundamental. Establishing clear communication protocols ensures everyone knows what to do and who to contact when an attack is detected. Automated mitigation tools can reduce downtime and damage by immediately initiating countermeasures to block or absorb malicious traffic. The quicker and more efficiently a team responds, the less likely the attack will result in severe consequences. It is also critical to conduct regular exercises and simulations to ensure the effectiveness of your reaction strategy. This preparation provides the team can act swiftly and decisively during an attack.
Building a Robust DDoS Mitigation Plan
Creating a comprehensive DDoS mitigation plan involves assessing risks, identifying critical assets, and implementing layered security measures. Begin with the risk assessment to identify potential weaknesses and assets requiring the highest security. This assessment will inform the necessary security measures to safeguard these assets effectively. Regularly reviewing and testing the plan ensures its effectiveness.
Future Trends in DDoS Mitigation
The cybersecurity landscape is continuously evolving. Integrating emerging technologies into DDoS mitigation techniques can enhance efficiency. These technologies aid in predictive analysis, allowing systems to recognize and respond to possible dangers before they become real. AI and machine learning algorithms can examine massive network data in real-time, discovering patterns and abnormalities that human analysts may overlook. By deploying these technologies, organizations can automate their defense mechanisms, making them quicker and more accurate in responding to threats. Staying current with these trends can provide organizations with the tools to maintain a robust defense against increasingly sophisticated cyber threats.
Conclusion and Best Practices
Effectively mitigating DDoS attacks requires a multi-faceted approach. Organizations can protect themselves from the disruptive impacts of these attacks by staying vigilant, employing various strategies, and continuously monitoring their network. Regular updates to your mitigation plan and staying informed on the latest trends ensure long-term security. Preparedness and proactive measures are vital to safeguarding against DDoS attacks. Incorporate best practices such as implementing layered security, establishing a rapid response plan, and leveraging advanced technologies like AI. By doing so, companies can create a resilient defense mechanism that can survive the changing nature of DDoS attacks. Remember, the goal is to respond to attacks and be prepared to prevent them, ensuring the continuity and reliability of essential services.
Leave a Reply