Revolutionizing Network Security: The Role of Secure Access Service Edge (SASE)
Introduction
By understanding the latest trends in network security, you can better protect your organization against escalating cyber threats. One game-changing approach is SASE. This model combines network security functions and WAN capabilities, revolutionizing network security worldwide. With cyber threats evolving continuously, adopting innovative security practices like SASE can significantly safeguard an organization’s data and resources.
SASE, or Secure Access Service Edge, aims to streamline and fortify network security by offering a comprehensive, cloud-delivered service model. Unlike traditional network security models that rely heavily on on-premise hardware and software solutions, SASE integrates multiple security functions into a single framework, simplifying the management and deployment process. This article will delve into SASE’s benefits, challenges, and future, providing a complete guide to improving your company’s network security.
What is SASE?
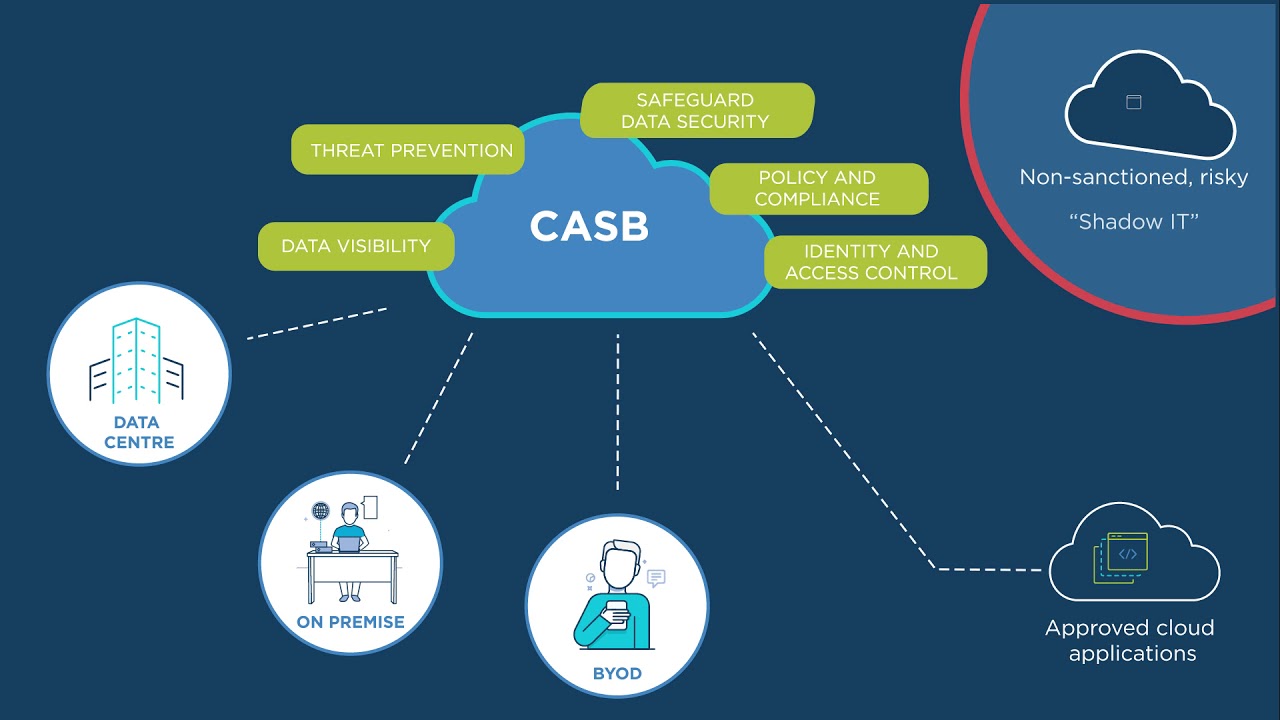
SASE, or Secure Access Service Edge, is a network architecture model that combines vast area network (WAN) capabilities with comprehensive network security functions like Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Firewall as a Service (FWaaS), and Zero Trust Network Access (ZTNA) into a single, cloud-delivered service model. This approach aligns network security and connectivity, simplifying management and enhancing security measures. By moving security services to the cloud, SASE eliminates the need for multiple-point solutions and makes applying consistent security policies across all network traffic easier.
Benefits of SASE
- Simplification of Network Security Management: By integrating various security functions under one roof, SASE significantly simplifies the management process, making it easier for IT teams to monitor and control. Traditional network architectures often require multiple security solutions, each with its management console, which can complicate the administration process. SASE consolidates these functions, providing a unified interface for comprehensive security management.
- Enhanced Performance and Lower Latency: SASE utilizes cloud infrastructure, which helps reduce latency and boosts network performance, providing a seamless user experience. By leveraging the global reach of cloud service providers, SASE can ensure that users are connected to the nearest Point of Presence (PoP), thus minimizing latency and improving the overall performance of network applications.
- Proactive Threat Detection and Response: The model proactively incorporates real-time data analytics to identify and counter security threats, improving organizational resilience against cyber attacks. Traditional security solutions often rely on reactive measures, identifying threats after they have occurred. SASE enables businesses to adopt a more proactive stance, using advanced analytics and AI to detect anomalous behavior and respond to threats in real-time.
- Scalability and Flexibility: SASE’s cloud-based nature allows organizations to scale their network security capabilities as needed, providing unparalleled flexibility. Whether a business is expanding its workforce, opening new branches, or adopting remote work policies, SASE can seamlessly scale to meet evolving demands. This flexibility is precious in today’s dynamic business environment, where the need for agile and responsive security solutions is more critical than ever.
Challenges and Limitations
Implementing SASE can be complex and may come with several challenges. These include integrating existing systems, initial costs, and potential latency issues. Adequate planning and a phased implementation approach can help businesses overcome these challenges, leading to substantial long-term benefits. For instance, integrating SASE into legacy systems may require changes to existing network architectures and processes, which could be time-consuming and costly. Moreover, organizations must ensure robust internet connectivity to support cloud-based security services without adding latency.
Implementing SASE in Your Organization
To successfully implement SASE, it’s essential to assess your organization’s current network and security posture, identify gaps, and develop a comprehensive strategy that includes training and continuous evaluation. Successful implementation often involves partnering with experienced vendors and utilizing detailed guidelines, such as those in this network security guide. Constant monitoring and iterative improvements play a crucial role in maintaining the efficacy of the SASE model. Businesses should also focus on change management, ensuring all stakeholders are informed and trained on the new security architecture. This includes IT staff and end-users, who must understand the latest security policies and how to comply with them.
SASE and Zero Trust Architecture
SASE often complements Zero Trust Architecture by ensuring that each access request is fully authenticated, authorized, and encrypted before granting access. By integrating these two models, a strong security setting is established, minimizing the chances of unauthorized entry or data breaches. Zero Trust principles reinforce the integrity of the SASE framework, providing an additional layer of security and control. In a zero-trust model, no user or device is trusted by default, whether inside or outside the network perimeter. This approach aligns well with the SASE model, which extends robust security policies to all network edges, ensuring comprehensive user and device protection.
Real-Life Examples of SASE in Action
Several organizations have successfully implemented SASE to enhance their network security. For example, a multinational financial institution experienced a 40% reduction in network management expenses and significantly improved threat response times after adopting SASE. This organization was able to streamline its security operations, reduce the complexity of its network infrastructure, and improve its overall security posture.
The Future of SASE
The adoption of SASE is expected to increase in the coming years as more organizations recognize the need for integrated, cloud-delivered network security solutions. AI and machine learning innovations will further enhance SASE’s capabilities, making it an indispensable tool for ensuring robust network security. AI-driven analytics will enable even more proactive threat detection and response, while machine learning algorithms can continuously improve the accuracy and effectiveness of security measures. The future of SASE points towards a more connected, secure, and efficient network environment, catering to the evolving needs of modern businesses. As digital transformation accelerates, adopting SASE is increasingly critical for organizations to safeguard their data and operations against cyber threats.
Stay in touch to get more updates & news on Glamouruer!